Lock It Up: Protecting Your Cloud Network
Several large-scale trends are shaping the modern IT workplace. Today’s workforce is decentralizing by shifting away from traditional office settings in favor of remote locations. At the same time, cybersecurity incidents are on the rise and new ransomware attacks hit our news feeds regularly.
While a decentralized workforce does provide many management benefits, it also creates a new problem: how to provide a secure, cloud-based computing environment for a team when corporate network protections are diminished.
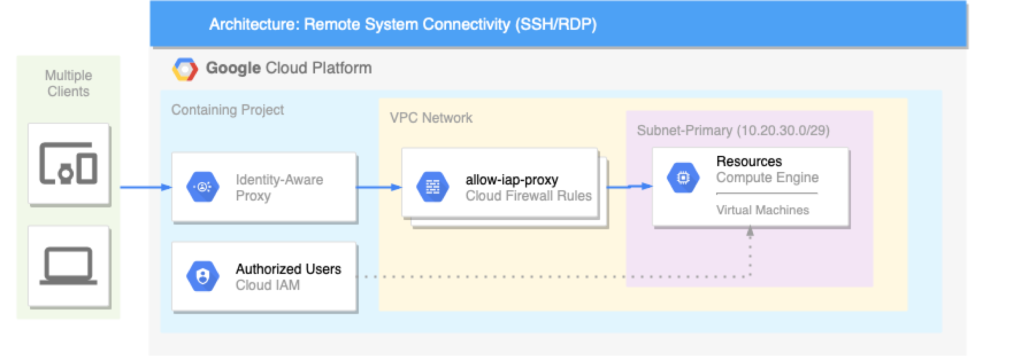
The traditional approach to solving this problem employs bastion or jump hosts. IT teams create exposed and specially hardened hosts within a cloud network, and users log in directly to those hosts to access protected network resources. While this approach effectively limits the external surface area of a cloud deployment, it also leaves some resources exposed to the internet. These bastion hosts incur additional resource costs and administrative overhead.
Fortunately, Google Cloud Platform (GCP) includes capabilities to implement a zero-trust security model known as BeyondCorp. BeyondCorp’s tools enable us to build a strong security model for our virtual workforce, spend less time managing network bastion hosts and deliver more differentiating work for our customers.
Context-aware access is a central component of GCP’s zero-trust security model. A key product used in deploying context-aware access is Cloud Identity-Aware Proxy (IAP). Cloud IAP creates secure connections to computing resources through secure shell (SSH) and remote desktop protocol (RDP) without the need to deploy bastion hosts.
Want to learn how? Click here to walk through the process of connecting to sample Linux and Windows VM instances through Cloud IAP.
As cool as our bastion-less configuration is, there are still some cases to be made for that operational pattern. In a future post, we will extend Cloud IAP with jump hosts to allow us to securely access private Google Kubernetes Engine clusters and private Cloud SQL instances.